- Upgrade your defenses, not your anxiety. Let’s Talk! Contact Us
BunnyLoader, latest malware-as-a-service, targets browsers & cryptocurrency
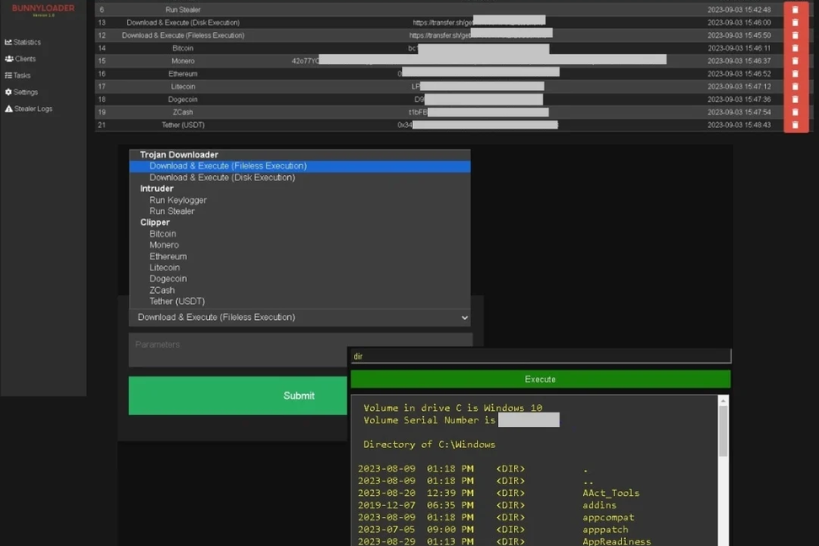
Cybersecurity experts have discovered yet another malware-as-a-service (MaaS) threat called BunnyLoader that's being advertised for sale on the cybercrime underground. "BunnyLoader provides various functionalities such as downloading and executing a second-stage payload, stealing browser credentials and system information, and much more," Zscaler ThreatLabz researchers said.
Among its other capabilities include running remote commands on the infected machine, a keylogger to capture keystrokes, and a clipper functionality to monitor the victim's clipboard and replace content matching cryptocurrency wallet addresses with actor-controlled addresses. A C/C++-based loader offered for $250 for a lifetime license, the malware is said to have been under continuous development since its debut on September 4, 2023, with new features and enhancements that incorporate anti-sandbox and antivirus evasion techniques.
"BunnyLoader is a new MaaS threat that is continuously evolving their tactics and adding new features to carry out successful campaigns against their targets," the researchers said. The findings follow the discovery of another Windows-based loader called MidgeDropper that is likely distributed via phishing emails to deliver an unnamed second-stage payload from a remote server. The development also comes amid the debut of two new information stealer malware strains named Agniane Stealer and The-Murk-Stealer that supports the theft of a wide range of information from breached endpoints.
Like this news article? Share it with others!
Source: Internet
© Copyright 2024 Proaxis Scitech Private Limited
Write a public review